Security
-

The Evolution of Zero Trust
Written by Dave Russell, Vice President, Enterprise Strategy at Veeam Around 18 months ago, I was writing about the “endless…
Read More » -

Ransomware Cryptocurrency Payments in 2023 Hit All-Time-High of $1.1Billion
After an encouraging decline in 2022, the ransomware landscape saw a major escalation in the frequency, scope, and volume of…
Read More » -
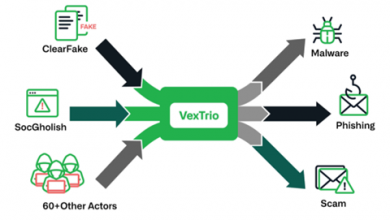
Infoblox Exposes VexTrio’s Extensive Criminal Affiliate Scheme
Infoblox has exposed crucial insights into the cybercriminal entity VexTrio, unravelling its intricate web of malicious connections with other cybercriminal…
Read More » -

Axis Communications to Show Off United Security Tech at Intersec Dubai 2024
Axis Communications has announced that it is participating in the 25th edition of Intersec. At the Axis exhibition stand, visitors can…
Read More » -

Veritas Technologies Launches Veritas 360
Veritas Technologies has announced Veritas 360 Defense, the first extensible architecture in its space that brings together leading data protection,…
Read More » -

Hytera Communications to Launch AI-Powered Push-to-Talk Devices at GITEX 2023
Hytera Communications will showcase its new generation of intrinsically safe two-way radios and smartphones at GITEX 2023, which is scheduled…
Read More » -

Cybersecurity Collaboration Holds Immense Significance in Today’s Threat Landscape
Ertug Ayik, the VP and MD of Middle East and Africa at HP, speaks about the security threat landscape in…
Read More » -

NETSCOUT Launches Real-time Adaptive DDoS Protection
NETSCOUT SYSTEMS, INC. has launched Adaptive DDoS Protection for its Arbor Threat Mitigation System (TMS) to dramatically improve the detection…
Read More » -

Cybercriminals Used Malware in 7 Out of 10 Attacks on Individuals in the Middle East
Positive Technologies analyzed attacks on individuals in Middle Eastern countries between 2022 and 2023. Malware was used in 70% of successful…
Read More »